Managed scanning
Semgrep managed scanning enables you to add repositories to your Semgrep org in bulk without adding or changing your existing CI workflows. Similar to Semgrep CI workflows, managed scanning also integrates into developer workflows through PR comments.
This is an alternative method to adding Semgrep in CI. Instead of adding a Semgrep job or workflow to your CI/CD pipeline, repositories are added to Semgrep AppSec Platform.
Feature maturity and support
- Managed scanning is in public beta for all existing Semgrep AppSec Platform users.
- Managed scanning supports hosted GitHub (GitHub.com) and GitHub Enterprise Server plans.
- This guide provides self-service enablement steps for hosted GitHub plans.
- To enable managed scanning on GitHub Enterprise Server, contact your technical account manager (TAM).
- Please leave feedback by either contacting your technical account manager (TAM) or through the Feedback form in Semgrep AppSec Platform's navigation bar.
- Managed scanning is available for all Semgrep products you have purchased, including:
- Semgrep Code
- Semgrep Supply Chain
- Semgrep Secrets
- Managed scanning performs both full scans and diff-aware scans when a developer creates a pull request.
- To receive Supply Chain findings, you must have a supported lockfile in your repository. Managed scanning does not support lockfile generation.
- For existing Semgrep projects, custom
semgrep.ymlconfigurations are not copied or detected when you use managed scanning. If you have additional build steps when scanning, use Semgrep in CI instead.
Security
Managed scanning requires read access to your code in GitHub for the repositories you choose to scan. Semgrep clones your repository at the beginning of every scan. Once the scan completes, the clone is destroyed and is not persisted anywhere.
The access to your code is facilitated by a private Semgrep GitHub app that you create and register in your GitHub organization.
- You are in control of the app and can revoke access to repositories at any time.
- You can limit access to specific repositories.
Managed scanning is specifically designed to limit the amount of time that code remains on our infrastructure.
Life cycle of a managed scan
- When a scan begins, Semgrep creates an ephemeral container and clones the repository into it.
- Semgrep runs the scan from that container. Diff-aware scans typically take seconds, while full scans can take minutes to hours to complete.
- The ephemeral container is immediately and automatically destroyed post-scan along with all contents in it.
Add a repository to Semgrep Managed Scanning
Part of the process of adding a repository includes creating and registering a public Semgrep GitHub app and a private Semgrep GitHub App.
- The public Semgrep GitHub app is required to easily add members of your GitHub org to your Semgrep org.
- The private Semgrep GitHub app is required to enable code access for managed scanning.
To view all permissions, see Pre-deployment checklist > Permissions for more information.
- In Semgrep AppSec Platform, click Projects.
- Click Scan new project > Semgrep Managed Scan.
- If you haven't completed the installation of public and private Semgrep GitHub apps, you are redirected to the Set up Managed Scans page, which facilitates the creation of both.
- Follow the steps in the page to create and register both a public and private Semgrep GitHub app.
- In the Enable Managed Scans for GitHub repos page, select the repositories you want to add to Semgrep Managed Scanning.
- Optional: If you don't see the repository you want to add, click Sync projects or click Check GitHub Access Configuration to ensure that you've granted Semgrep access to at least one repository.
- Select the repositories you want to scan from the list.
- Click Enable Managed Scans.
You have finished setting up a Semgrep Managed Scan.
- After enabling managed scanning, Semgrep performs a full scan in batches on all the repositories.
- Once a repository has been added to Semgrep AppSec Platform, it becomes a project. A project in Semgrep AppSec Platform includes all the findings, history, and scan metadata of that repository.
- Projects scanned through managed scanning are tagged with
autoscan.
Troubleshoot your Semgrep GitHub app installation
A complete installation is displayed in the Source Code Manager entry as follows:
 Figure. Semgrep AppSec Platform > Settings > Source Code Managers displaying a completed managed scanning set-up.
Figure. Semgrep AppSec Platform > Settings > Source Code Managers displaying a completed managed scanning set-up.
You can also confirm a complete installation through your GitHub settings page, which should have two Semgrep apps:
 Figure. GitHub > Settings > Applications displaying both Semgrep apps. The private Semgrep app follows the convention Semgrep Code - YOUR_ORG_NAME.
Figure. GitHub > Settings > Applications displaying both Semgrep apps. The private Semgrep app follows the convention Semgrep Code - YOUR_ORG_NAME.
If the page doesn't display any repositories
- Ensure you have provided access to both the private and public Semgrep GitHub to the repositories you want to scan by following the steps in Permissions and synchronicity.
- In Semgrep AppSec Platform, click Projects.
- If the page doesn't display the repository you want to add, click Can't find your project? > Sync projects.
- If the page doesn't display any repositories, click Sync projects.
- Optional: Perform a hard refresh (Ctrl+F5 or Cmd+Shift+R).
Repositories must be accessible to both the public Semgrep GitHub app and the private Semgrep GitHub app.
Convert or migrate an existing Semgrep CI job
You can immediately add any existing project to managed scanning.
- Follow the steps in Add a repository.
- Delete the
/.github/workflows/semgrep.ymlfile in your GitHub repository.
Semgrep preserves your findings, scans, and triage history.
Default configuration
By default, projects on managed scanning are configured with:
- Weekly full scans of the entire repository. When a project is first added to managed scanning, the AppSec Platform performs an initial scan and then sets a random time up to 6 days after to perform a weekly full scan. Each weekly scan occurs on that same day and time.
- Diff-aware scans on pull requests that run on every PR. These diff-aware scans follow the rule modes set in your Policies, ensuring that developers are only notified of findings from high-signal rules you place in Comment or Block mode.
Scan management and configuration
Manually run a full scan
- In Semgrep AppSec Platform, click Projects.
- Search for your repository's name.
- Click the gear icon to access the settings page for that repository.
- Click Run a new scan.
Disable diff-aware scans on PRs
- In Semgrep AppSec Platform, click Projects.
- Search for your repository's name.
- Click the gear icon to access the settings page for that repository.
- Click the toggle for diff-aware scans.
Remove a repository
- In Semgrep AppSec Platform, click Projects.
- Search for your repository's name.
- Click the gear icon to access the settings page for that repository.
- Click the dropdown at the header and click Delete project.
Revoke Semgrep's access to your repositories
Remove the private app
The following steps revoke the code access you previously granted Semgrep for all repositories you selected.
- In Semgrep AppSec Platform, click Settings > Source Code Managers.
- On the entry of the SCM you want to remove, click Remove app.
- Click Remove to confirm.
Limit access to specific repositories
- Navigate to your GitHub settings page.
- On the entry of your private Semgrep GitHub app, click Configure.
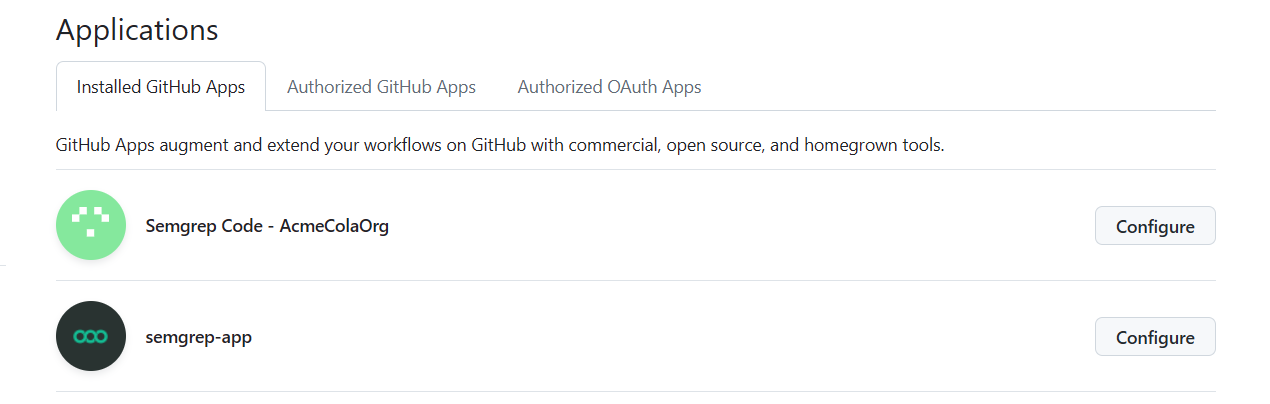
- Under Repository access, de-select the repositories you no longer want to grant Semgrep access to.
Appendices
Permissions and synchronicity
Both the public and private Semgrep GitHub app must have access to the repositories you want to scan.
To view the repositories you have granted access to:
- Navigate to your GitHub settings page.
- On the entry of your public Semgrep GitHub app, typically semgrep-app, Click Configure.
- Review the repositories under repository access.
- Perform steps 2 and 3 on the entry of your private Semgrep GitHub app.
Scan logs and statistics
Scan statistics, such as how many of your repositories are being scanned, the scan success rate, and so on, can be provided once a week upon request. Contact your Semgrep account manager to request scan statistics.
Not finding what you need in this doc? Ask questions in our Community Slack group, or see Support for other ways to get help.