Single-sign on (SSO) configuration
- You have gained the necessary resource access and permissions required for deployment.
- You have created a Semgrep account and organization.
- For GitHub and GitLab users: You have connected your source code manager.
The only required steps to ensure that users are added to Semgrep AppSec Platform are on the side of the SSO provider. After setting up SSO, users are able to sign in to your Semgrep organizations by entering their SSO credentials.
Semgrep supports SSO through OpenID Connect / OAuth 2.0 and SAML 2.0.
OpenID Connect / OAuth 2.0
To set up SSO:
- In Semgrep AppSec Platform, click Settings > Access > SSO, and then select Add OpenID SSO.
- Copy the
Redirect URL.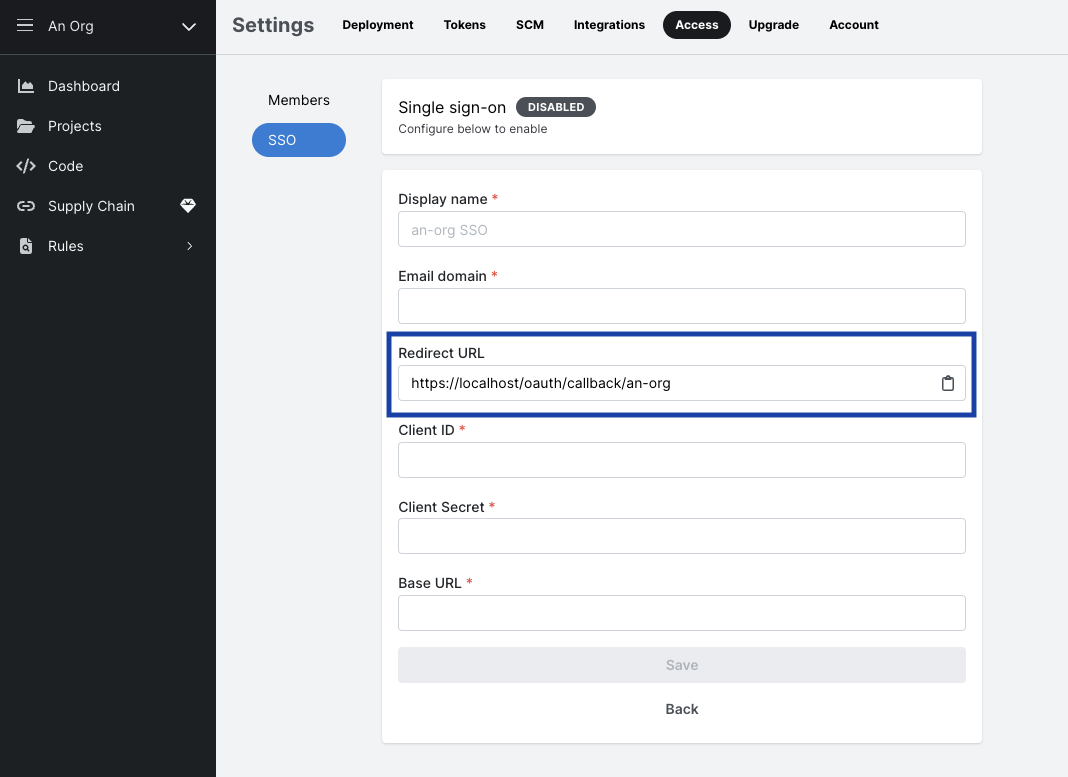
- Generate a
Client IDandClient Secretthrough your authentication provider and paste them.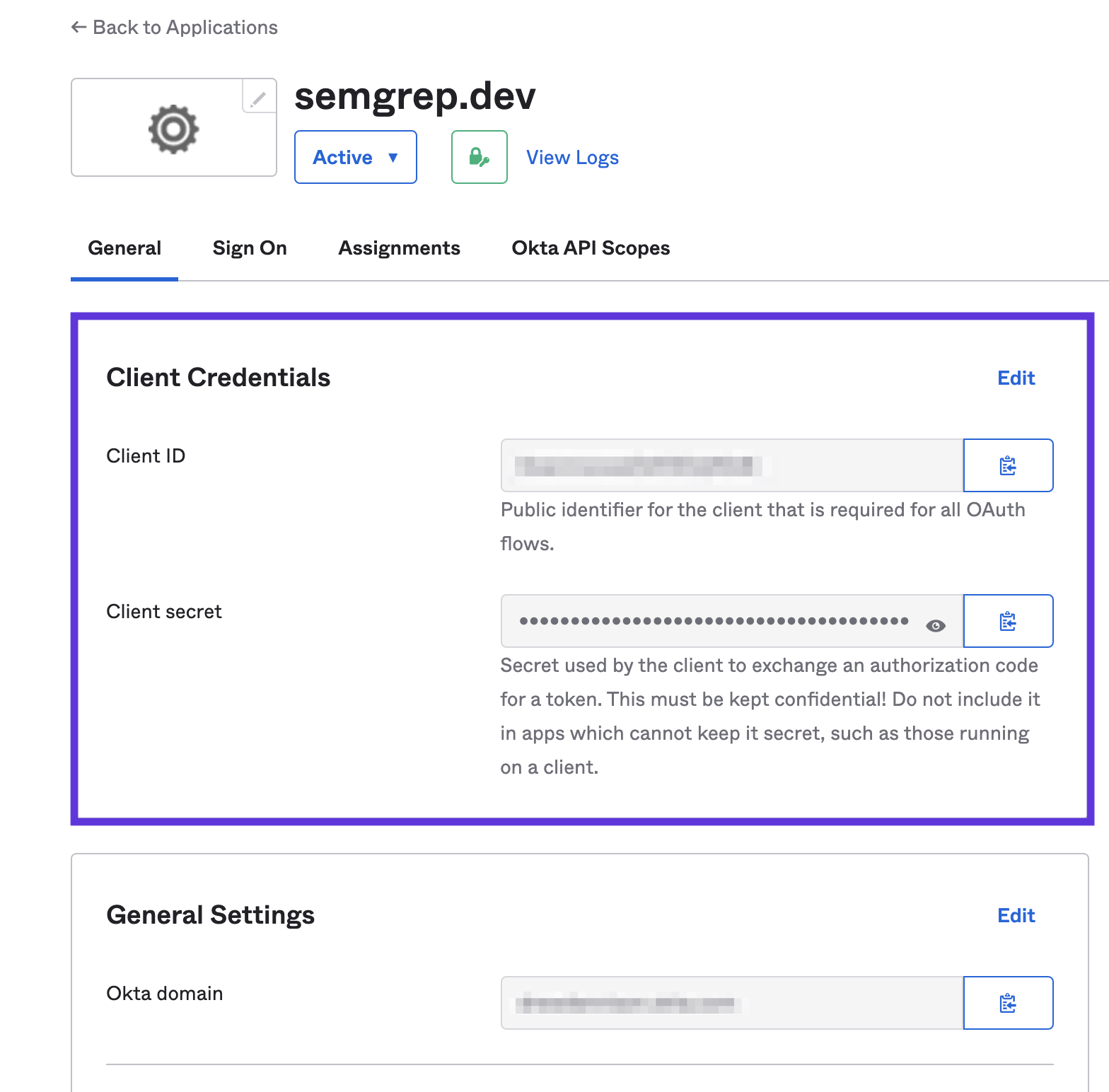
- From your authentication provider, copy the values for
Base URL/DomainandEmail Domainto Semgrep's Configure SSO: OpenID tab.Base URL/DomainisOkta domainfor Okta SSO. - Provide a descriptive
Display Name.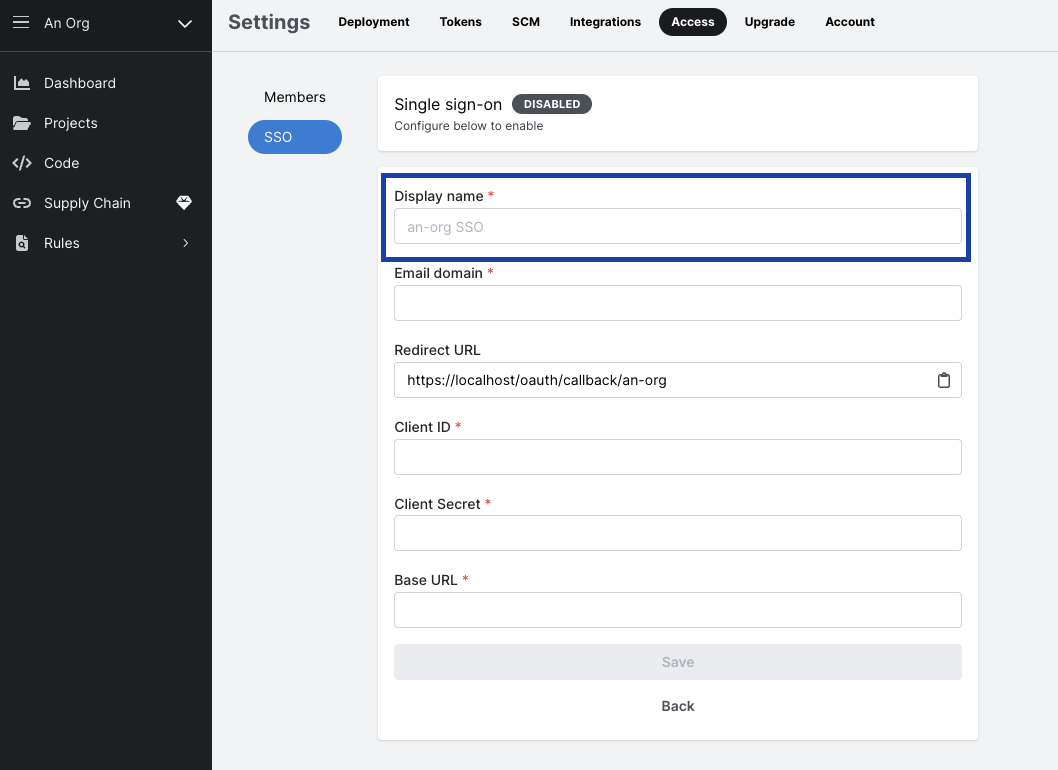
In case you encounter issues during the setup process, please reach out to support@semgrep.com for assistance.
SAML 2.0
SAML2.0 is configured through Semgrep AppSec Platform.
To set up SSO:
- From your authentication provider, create the SAML app.
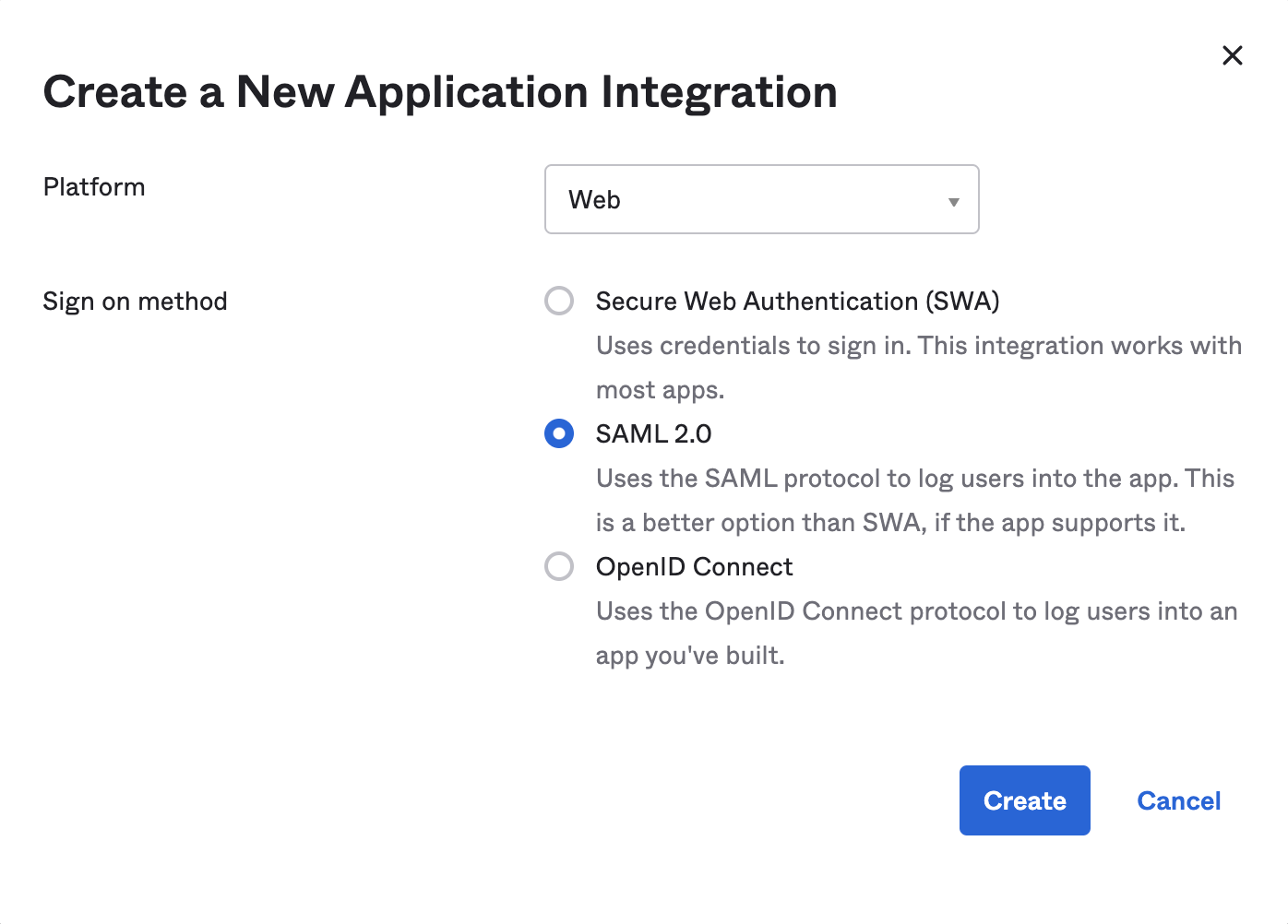
- From the App Dashboard, click Settings > Access > SSO
- Copy the
Single sign on URL, andAudience URI. Paste the values as needed in your authentication provider. The Provider ID value will be your organization's slug in Settings > Deployment,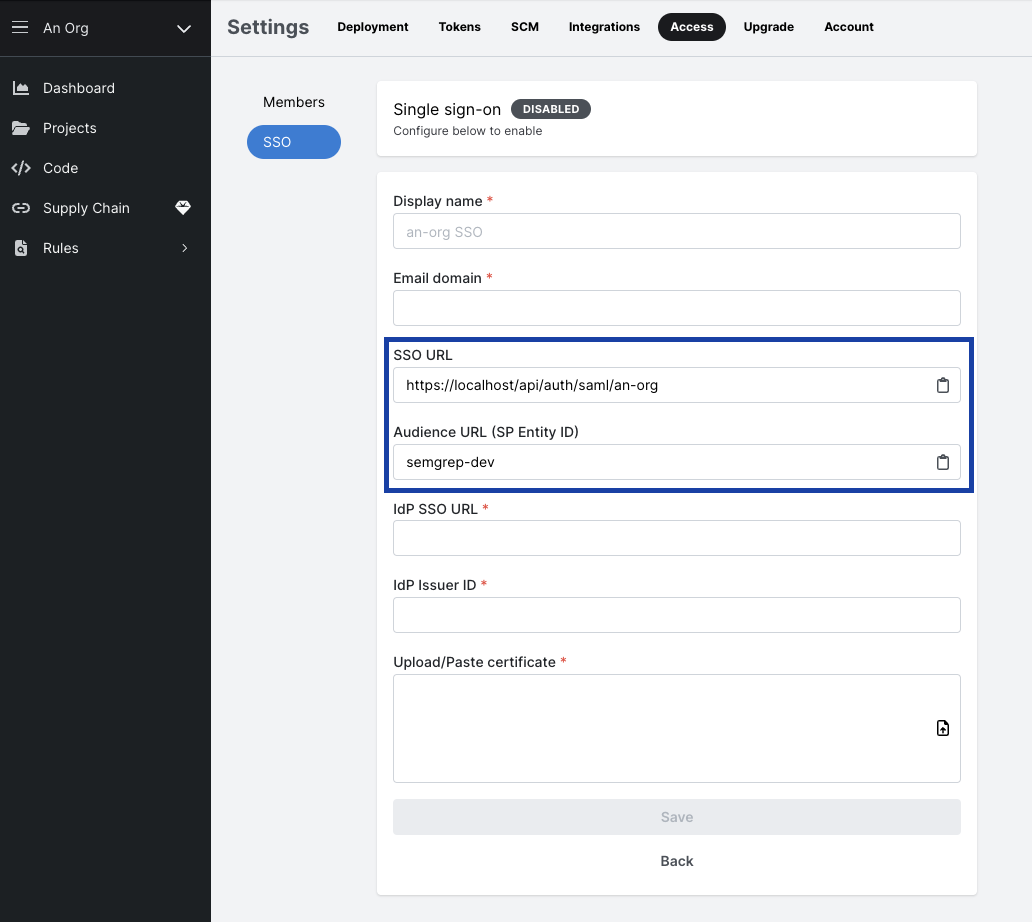
- From your authentication provider, add in two attribute statements
nameandemail.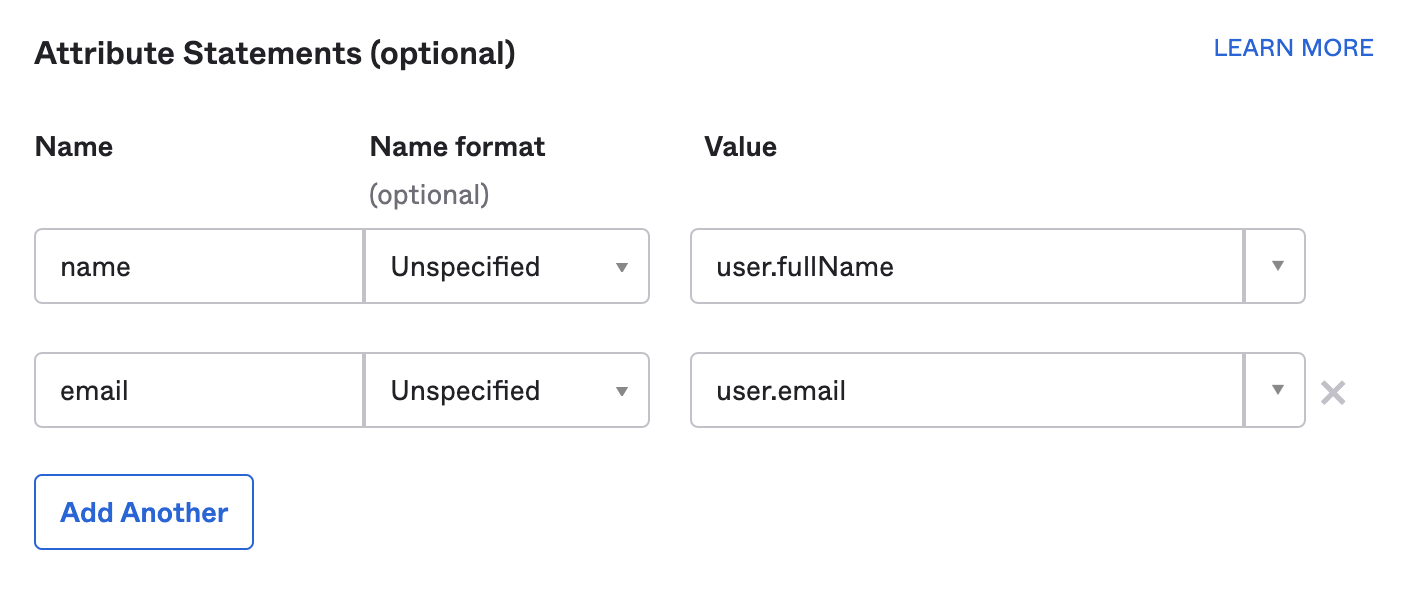
- From your authentication provider, copy your
IdP SSO URL,IdP Issuer ID, andX509 Certificateto Semgrep's Configure SSO: SAML tab.
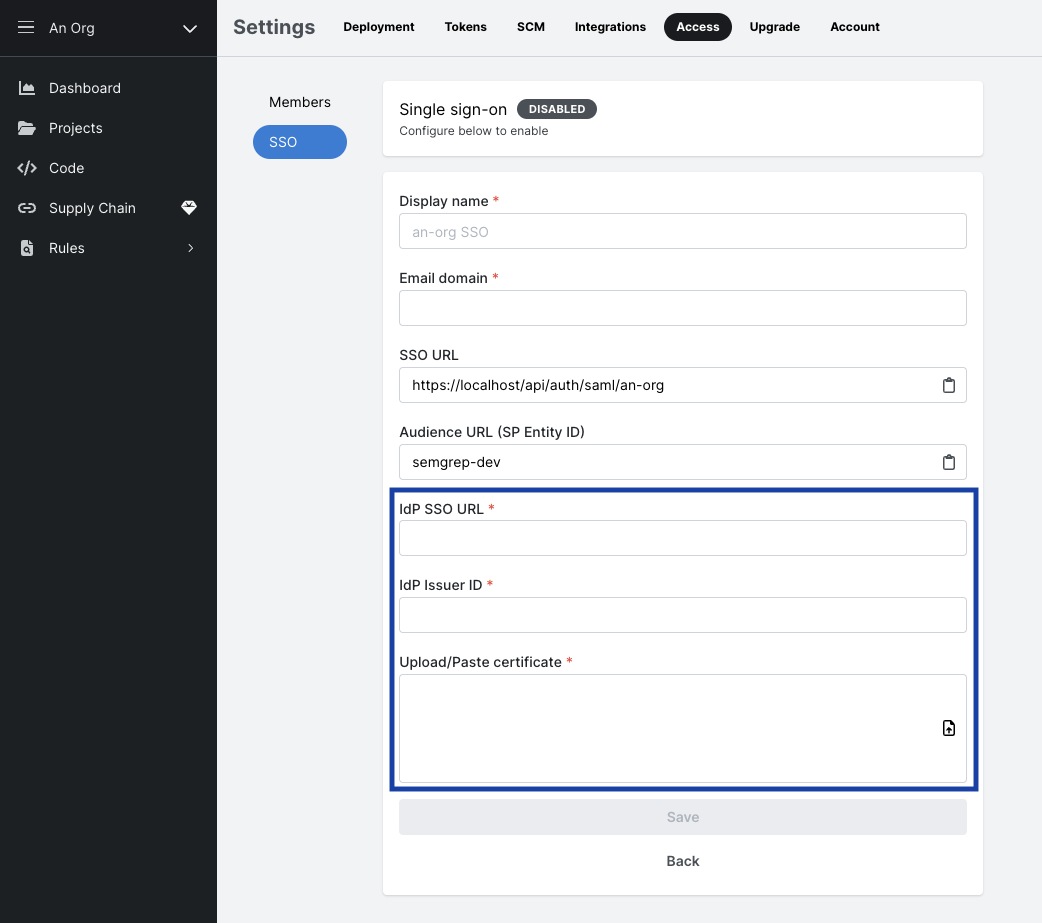
- Provide a descriptive
Display Name.
If you encounter issues during the setup process, reach out to support@semgrep.com for assistance.
Set up SAML SSO with Microsoft Entra ID
- An existing Microsoft Entra ID account.
- Sufficient permissions within Microsoft Entra ID to create enterprise apps. See Microsoft Entra ID roles.
Setting up SAML SSO using Microsoft Entra ID consists of the following general steps:
- Create a custom enterprise app within Microsoft Entra ID.
- Set up SAML SSO for your new enterprise app.
- Add users to your new enterprise app.
Create a custom enterprise app
- Sign in to the Microsoft Entra admin center.
- Use the search bar to find and navigate to enterprise applications.

- Click New application > Create your own application. A menu appears.

- Name your new application something like
Semgrep SAML. - Select Integrate any other application you don't find in the gallery (non-gallery).
- Click Create. This takes you to your new enterprise application's page.
You have now created a custom enterprise app for Semgrep to integrate with Microsoft Entra ID. This enables you to set up SAML SSO.
Set up SAML SSO for your new enterprise app
- From your new enterprise app's page, go to Single-sign on > SAML.

- When prompted to Select a single sign-on method, select SAML. You are redirected to the SAML-based Sign-on page.

- In the Basic SAML Configuration section, click Edit. Provide the Entity ID and Reply URL. You can retrieve these values from Semgrep AppSec Platform by performing the following steps:
- Log in to Semgrep AppSec Platform and navigate to Settings > Access > SSO page.
- Click Add SAML2 SSO.
- Copy the Audience URL value from Semgrep AppSec Platform. Return to Basic SAML Configuration. Click Add identifier to paste this value as the Identifier (Entity ID).
- Copy the SSO URL value from Semgrep AppSec Platform. Return to Basic SAML Configuration. Click Add reply URL to paste this value as the Reply URL (Assertion Consumer Service URL).
- Click Save and close out of Basic SAML Configuration.
- In the Attributes and Claims section, click Edit. You must add two claims. To add your first claim:
- Click Add new claim.
- Enter
namein the Name field. - For the Source attribute drop-down box, select
user.displayname. - Click Save.
- To add your second claim:
- Click Add new claim.
- Enter
emailin the Name field. - From the Source attribute drop-down box, select
user.mail. - Click Save.
- Close out of Attributes & Claims.
- Navigate to Semgrep AppSec Platform, and provide the values required by the SAML2 form:
- Provide the Display name and the Email domain you are using for the integration.
- Copy the Login URL value from Microsoft Entra ID and paste it in into Semgrep AppSec Platform's IDP SSO URL field.
- Copy and paste the Microsoft Entra ID Identifier value into Semgrep AppSec Platform's IdP Issuer ID field.
- In Entra ID's SAML-based Sign-on page, click Download to obtain the Certificate (Base64).
- In Semgrep AppSec Platform, under Upload/Paste certificate, click Browse and then select the certificate you downloaded.

- Click Save. When prompted to confirm your SSO updates, click Update.
You have now set up SAML configuration between Microsoft Entra ID and Semgrep AppSec Platform.
Add users to your new enterprise app
To add users to the application in so they can log in with their domain emails, refer to Assign users and groups to an application.
Not finding what you need in this doc? Ask questions in our Community Slack group, or see Support for other ways to get help.