Triage and remediate dependency findings
Perform triage and remediation on your open source dependencies through the Supply Chain page. This page displays relevant scan data through three tabs:
- Vulnerabilities
This tab enables you to:
- View reachable vulnerabilities in your repositories through links to specific lines of code.
- Filter vulnerabilities by severity, reachability, status, transitivity, and other attributes.
- Understand how to remediate vulnerabilities by providing versions to upgrade to.
- Track the process of resolving vulnerabilities by adding links to Jira issues and pull requests.
- Advisories
- This tab displays the latest Common Vulnerabilities and Exposures (CVEs) that are covered by Semgrep Supply Chain rules. Use this tab to see the CVEs that Semgrep Supply Chain can detect.
- Dependencies
- This tab displays information about all of your dependencies across all onboarded repositories.
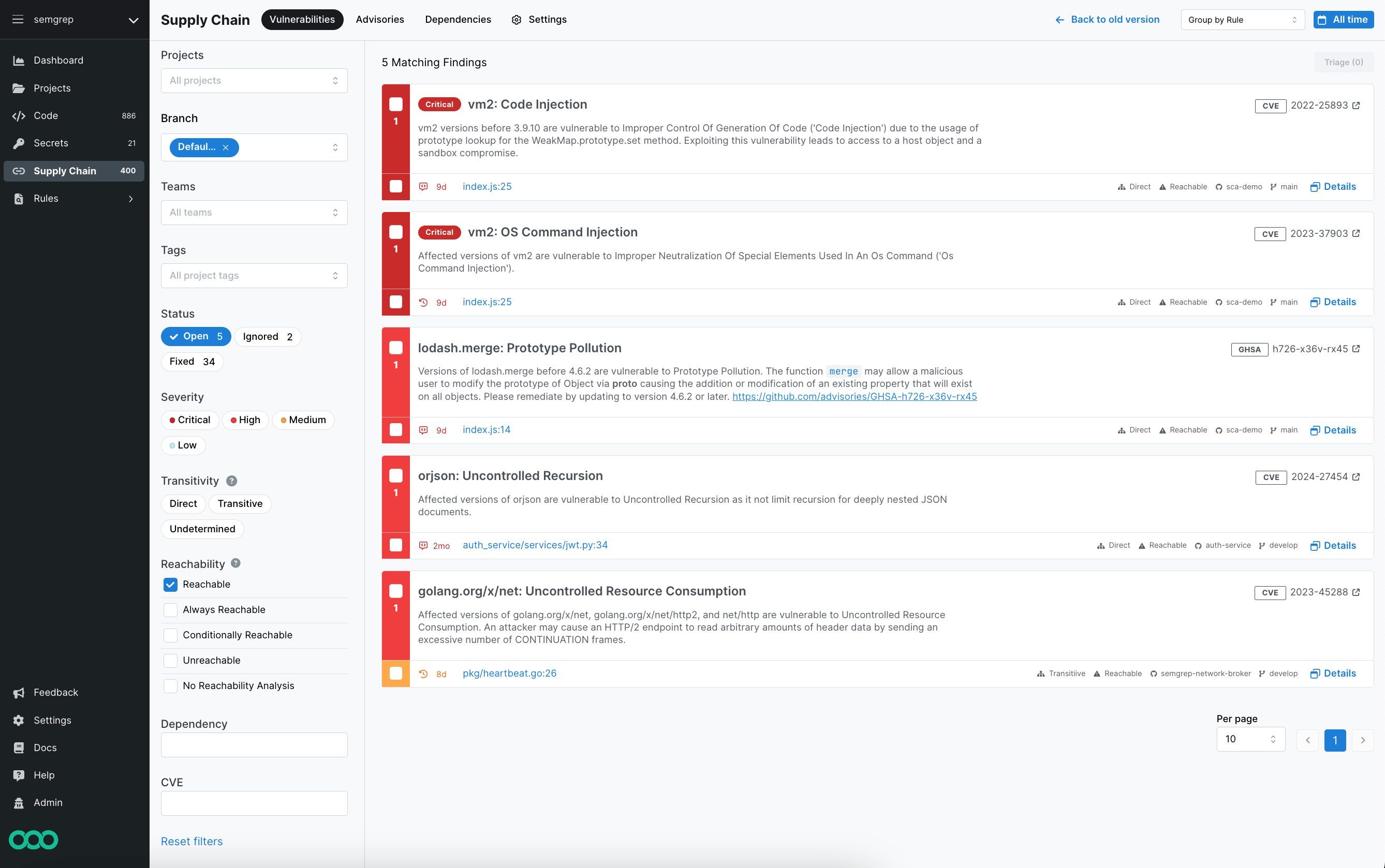 Figure 1. Semgrep Supply Chain Vulnerabilities page.
Figure 1. Semgrep Supply Chain Vulnerabilities page.
Assess and triage dependency findings and usages
At least one repository that scans for dependencies through Semgrep Supply Chain. See Scan third-party dependencies.
To view the latest Semgrep Supply Chain findings, click Supply Chain. You can view findings individually or grouped by the rule that identified the finding. A specific finding in the code is called a usage. Vulnerability entries are sorted as cards by severity from critical to low, then from oldest to newest.
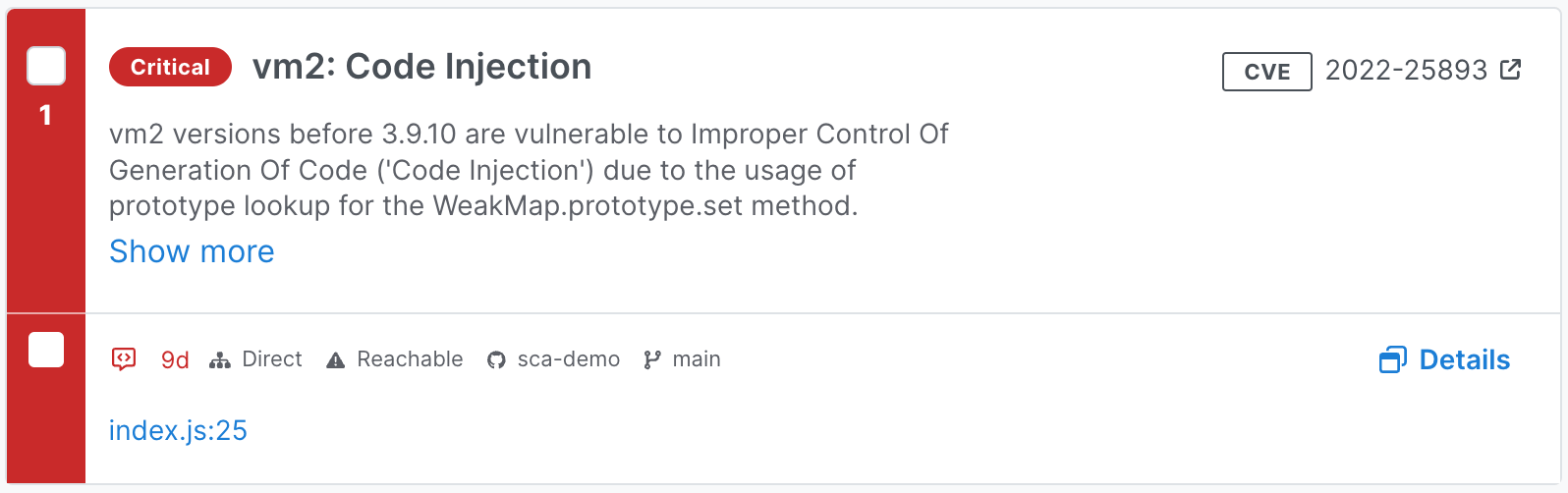 Figure 2. A single vulnerability entry in Semgrep Supply Chain.
Figure 2. A single vulnerability entry in Semgrep Supply Chain.
You can also view the findings individually by clicking on the drop-down box on the header and clicking No grouping.
Assessment actions
To assess your findings, Semgrep Supply Chain provides the following methods:
| Assessment action | Method |
|---|---|
| View specific pattern matches in your codebase. | Click the link provided in the vulnerability entry to see where the issue appears in the source code. |
| View specific CVE entries in cve.org. | Click the vulnerability's CVE badge. |
| View safe versions to upgrade your dependencies. | Visible on the vulnerability entry. |
| Filter vulnerabilities. | Click any of the filters available. Refer to the following table for filtering information. |
Filters
Use filters to narrow down your results. The following criteria are available for filtering:
| Filter | Description |
|---|---|
| Projects | Filter by repositories connected to your Semgrep account. |
| Branch | Filter by findings in different Git branches. |
| Teams | Filter for findings in projects to which the specified teams are associated with. Available only to organizations with Teams enabled. |
| Tags | Filter for findings based on the tags associated with the project. |
| Status | Filter the triage state of a finding:
|
| Severity | Filter by the severity of a finding. Filters are based on the severity of a vulnerability. Semgrep Supply Chain rules use severity values set by the GitHub Advisory Database. |
| Transitivity | Filter by the transitivity of the finding.
|
| Reachability | Filter by exposure, or whether the finding is reachable or not.
|
| Dependency | Filter for findings based on the name of the dependency involved. |
| CVE | Filter based on the CVE assigned to the finding type. |
Remediate true positives
Remediate (or resolve) true positives in Semgrep Supply Chain through the following methods:
- Update the dependency to a safe version that does not contain the vulnerability.
- Remove the dependency and refactor all usages in the codebase.
Remove the dependency and refactoring code
Another method to remediate vulnerabilities is to remove the dependency entirely and refactor code. Upon merging any dependency removals, Semgrep Supply Chain scans the PR or MR, detects the changes in your lockfile, and updates the status to Fixed.
Ignore findings
The Vulnerabilities tab allows you to identify the reachable, true positives so that you can fix or resolve the related issues. However, you can choose to ignore any false positives, acceptable risks, or deprioritized findings due to some factor. To do this:
- Select one or more findings.
- Click Triage.
- Select Ignore and click Continue.
- Select an Ignore reason, provide a optional comment, and click Ignore.
View Semgrep Supply Chain's total CVE coverage
The Advisories tab displays all the CVEs that Semgrep Supply Chain can detect. Click the individual entry to see the code pattern that the Advisory detects. The Advisories tab displays both lockfile-only and reachability rules.
Semgrep ingests CVE information and security advisories from sources such as Reviewed GitHub Security Advisories to ensure effective rule coverage. Semgrep processes new information at least once per day to:
- Generate rules for new security advisories;
- Update rules based on changes to existing security advisories.
Not finding what you need in this doc? Ask questions in our Community Slack group, or see Support for other ways to get help.