Announcing GA for Semgrep Assistant
When we first started experimenting with AI during an internal hack-a-thon, we quickly realized that we wanted to hold off on augmenting our SAST engine with AI inputs - we wanted to take a different approach and see if generative AI could first serve as a productivity multiplier for core AppSec workflows.
We asked countless customers the following question to help inform our development of Semgrep’s AI capabilities:
“If you had 10 more AppSec engineers on your team, what would they be doing?”
We wanted our AI-powered features to feel indispensable in the day-to-day work and productivity of our users (AppSec engineers and developers). Because of this, we went with the name “Semgrep Assistant”.
Fast forward to today - when customers tell us what they would task 10 additional security engineers with, our usual response is:
“Semgrep Assistant can actually do most of the things you just mentioned, and it’s free for all Semgrep customers”
With that level of confidence, we felt we were ready to officially launch Semgrep Assistant as GA!
This means that any Semgrep customer on a Team or Enterprise plan can use Assistant to amplify the impact of each of their security engineers, while empowering the developers they work with.

Our Philosophy around AI
At Semgrep, we know that feeding a repository’s worth of code to an LLM (even a model fine-tuned for SAST purposes) and having it spit out actionable security findings is a myth (as of today). SAST vulnerabilities are too contextual, and the signal-to-noise ratio would render any true findings, amongst the sea of false positives, useless.
This is why when most security products add an "AI element", it's usually purely additive and involves tacking on a generative auto-fix solution to an IDE plugin, with no actual strategic integration or value-add to the broader product.
Given the current state of LLMs and their ability to understand code within certain context windows, we found AI perfect for accelerating and automating the human processes that happen before and after a scan, but struggled to find a situation where it could come close to matching or improving on our Pro Engine’s performance.
As AI continues to improve in its ability to understand code, we’re lucky to have a fantastic core analysis engine that is transparent and easy to extend upon, so we can be among the first to innovate in that direction as well.
The magic of Semgrep Assistant
Turning Semgrep Assistant on should feel like magic for both developers and security folks, with generative suggestions for prioritization, triage, and remediation automatically surfacing in the right places at the right time.
Auto-triage:
Assistant uses AI’s understanding of code, alongside prompts specific to Semgrep rules, to determine when security findings are false positives. Triage recommendations are shown in the Semgrep app and in PR comments for developers. Humans agree with Assistant’s auto-triage recommendation 97% of the time.
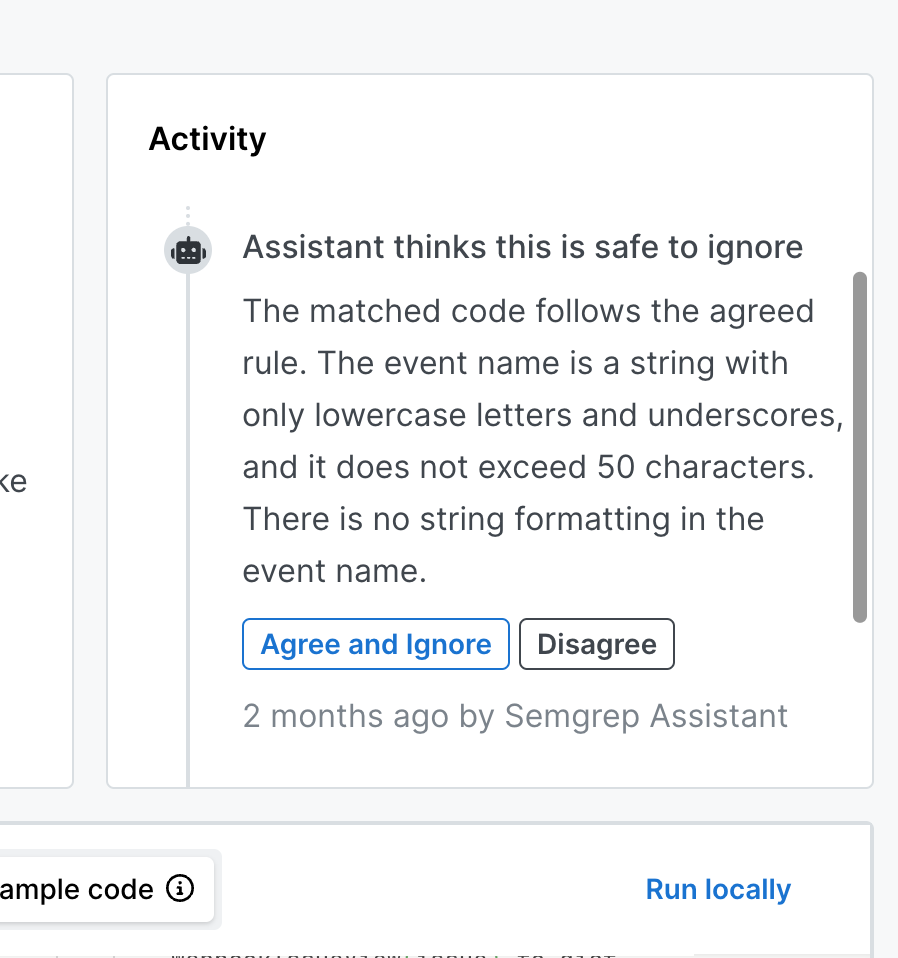
False positive ID with explainability
Auto-fix:
When Assistant identifies a true positive, it recommends an autofix for remediation. Recommendations include context and reasoning specific to the finding that allow developers to quickly understand and verify the correctness of a fix.
This also ensures that developers are still able to upskill and build their knowledge of secure design over time (learning about a vulnerability is a much less painful process when it's contextual and you aren’t forced to navigate to an external page and read static documentation).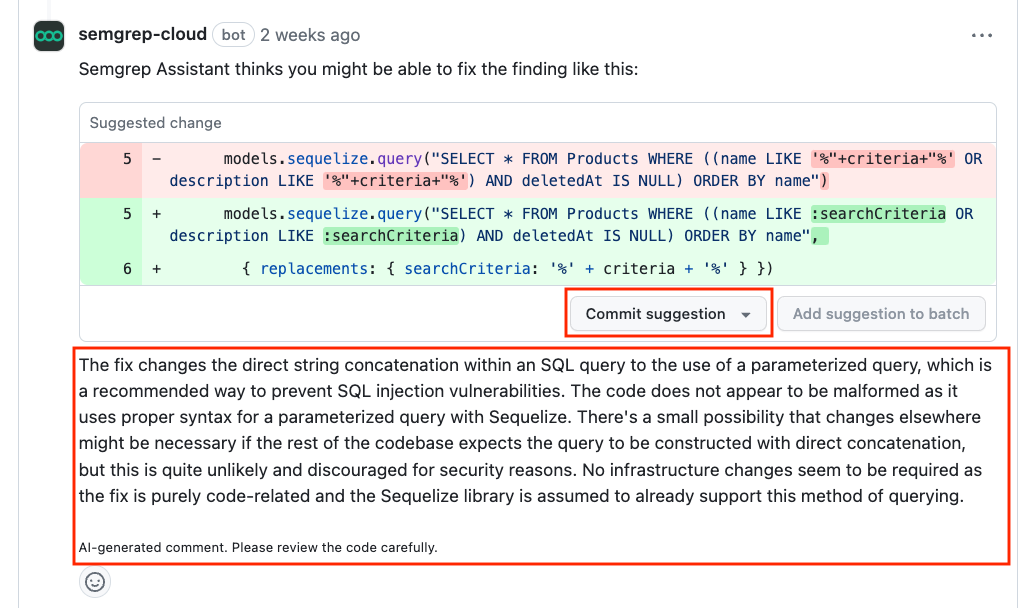
An assistant auto-fix recommendation (note the explainability and verifiability). Users can commit changes with the click of a button
Custom rule-writing (beta):
Assistant can write custom rules to find patterns or vulnerabilities specific to your codebase - all you need to provide is one example of “bad code”, one example of “good code”, and a prompt describing what you want the rule to do in human language.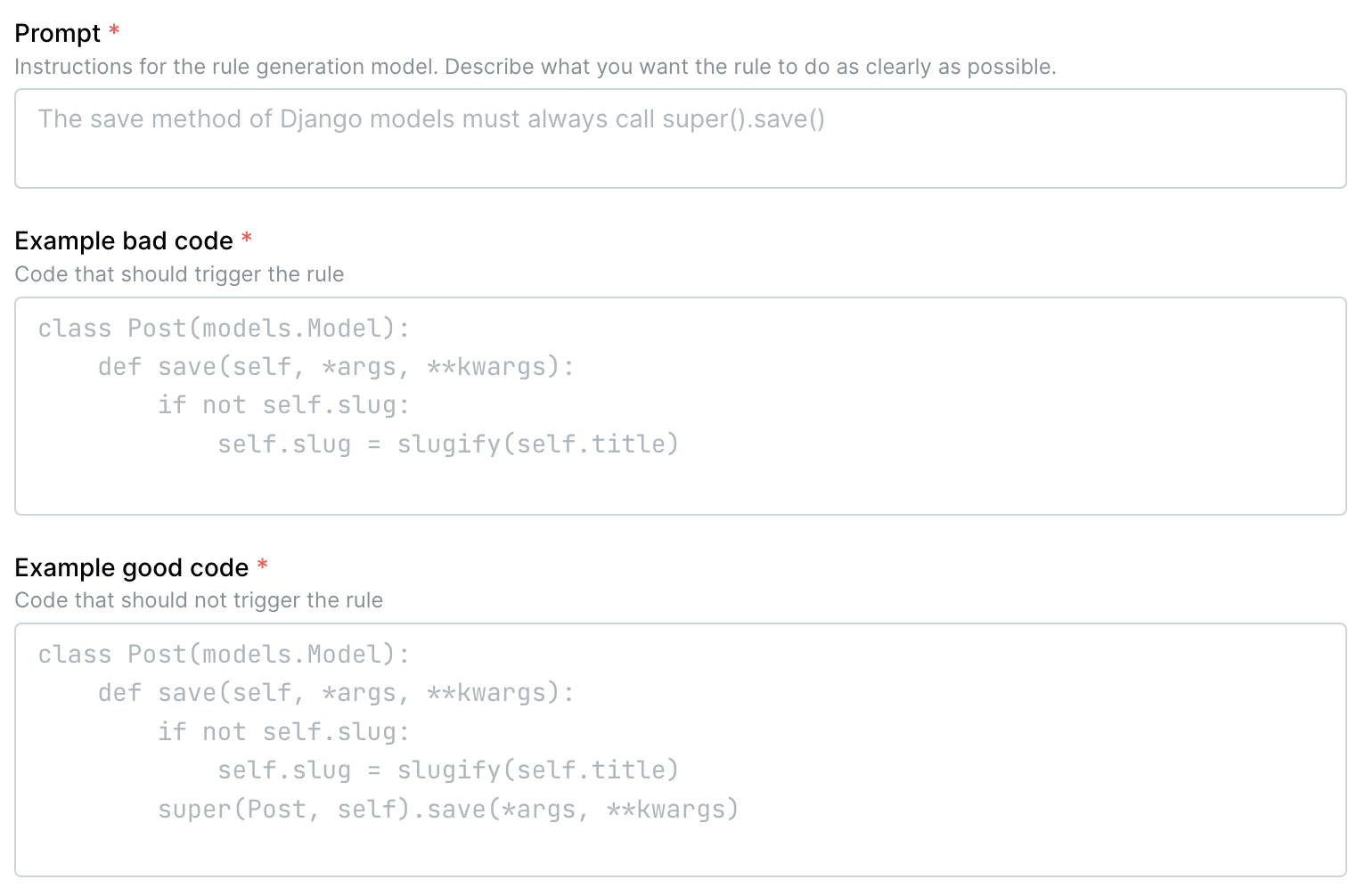
Semgrep Assistant's rule-generation UI
There's an endless amount of use cases here - every AppSec team probably has dozens of organization-specific guardrails that they've wanted to codify, and now have the means to.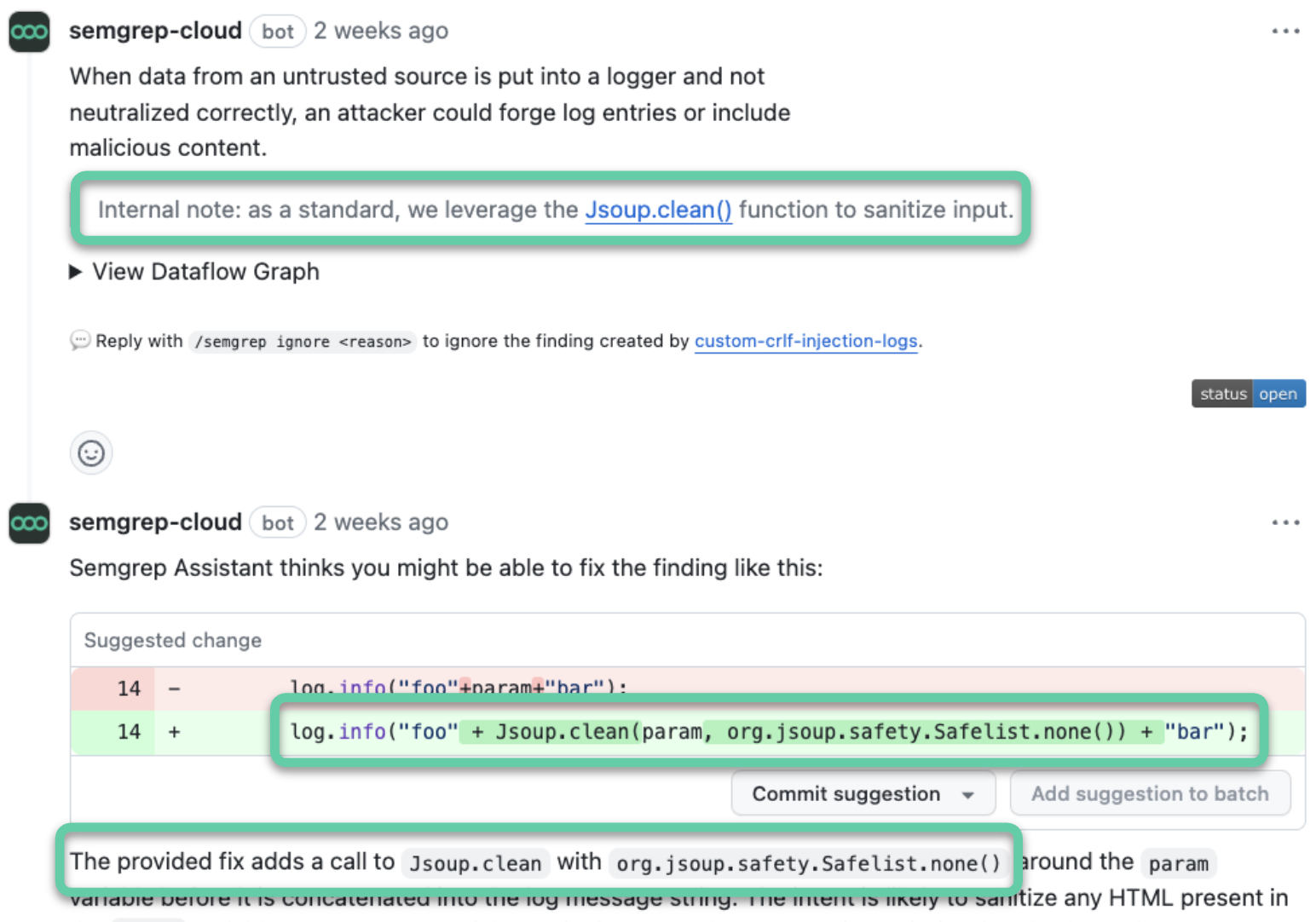
An assistant-generated rule in action, with an assistant auto-fix recommendation for the finding
Prioritization:
Semgrep Assistant provides users with a priority inbox (this feature is in early access), bubbling up key, actionable issues that AppSec teams should prioritize based on a variety of factors.
One such factor is the component tag of a finding - Assistant tags code findings based on their function/category, helping users answer questions like "does this finding have implications on user authentication?"
Component tags include infra, user data, user authentication, personally identifiable information, payments, etc.
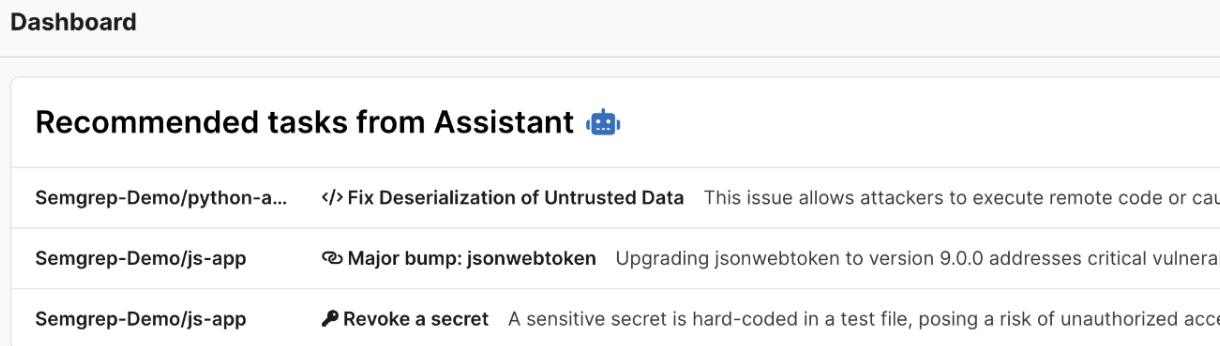
Example priority inbox tasks across Semgrep Code, Supply Chain, and Secrets
Continuous recommendations = continuous improvement
The Assistant features we’ve covered thus far are things that will benefit users the moment Assistant is turned on - what we’re often more excited about however, is the broader value that Assistant can provide by synthesizing data across workflows and deriving actionable recommendations, policies, and rules for AppSec teams.
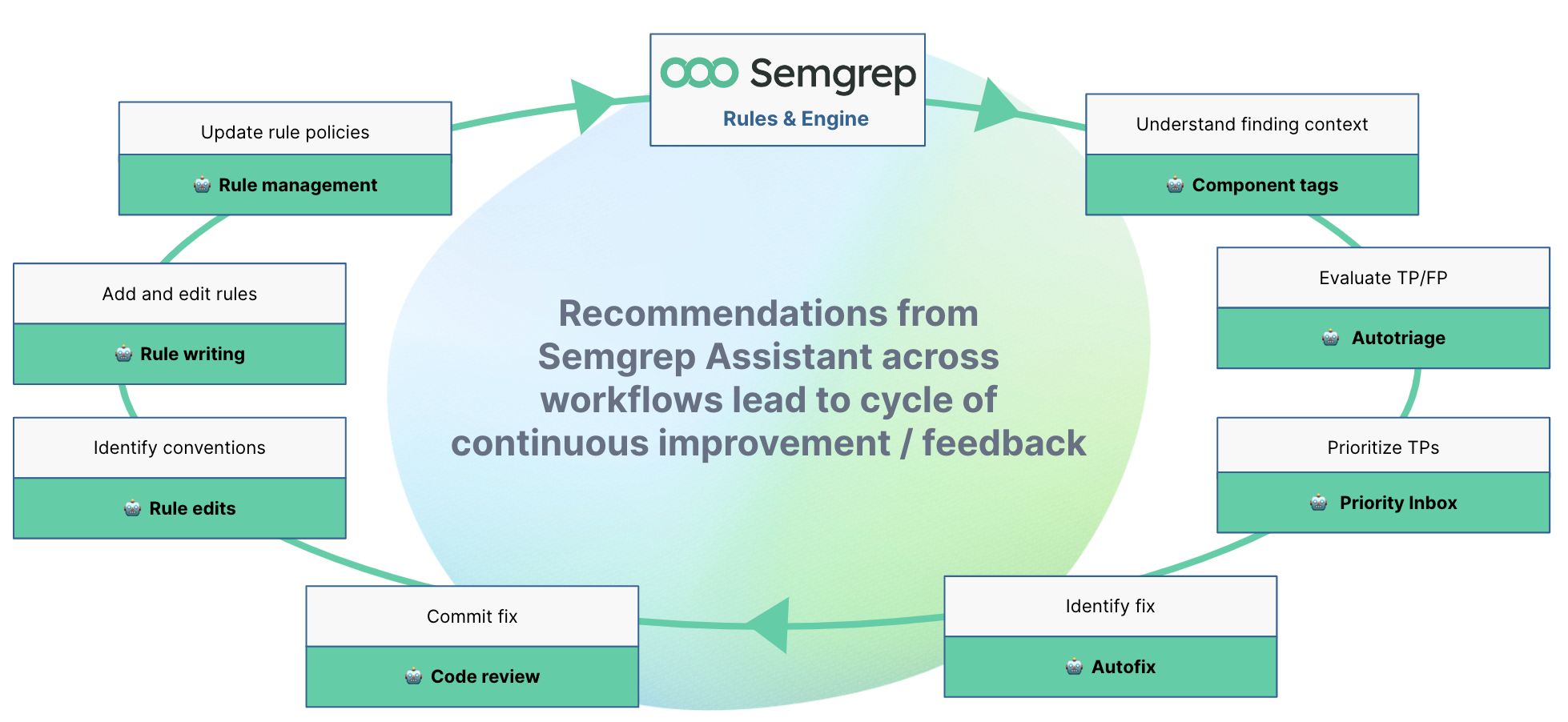
We think a highly customized instance of Semgrep is easily the best code security solution available on the market, and Assistant makes it easy for under-resourced teams to start creating custom rules, tweaking policies, etc.
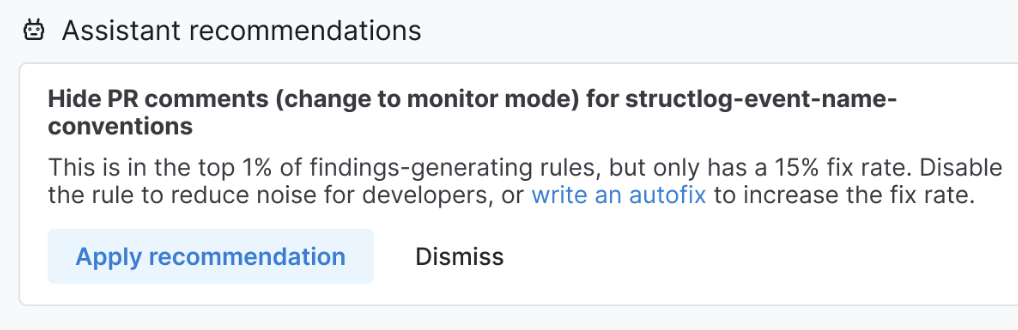 Rule policy recommendations (design mock/not implemented yet)
Rule policy recommendations (design mock/not implemented yet)
Wrapping up
Beyond making customization more accessible, our plan is eventually for Assistant to encourage, recommend, and help you write rules for the guardrails / practices that are best suited to your codebase.
Visit the Assistant product page to learn more, or sign up to get started today!


